Critical SAP: The recently discovered CVE-2025-31324 vulnerability in SAP NetWeaver has been swiftly patched after being identified as a significant security risk. This flaw, which was actively exploited in the wild, posed a severe threat to organizations running vulnerable SAP applications. With the patch now released, users are urged to update their systems immediately to prevent potential exploitation and safeguard critical business processes.
⚠️Verify if You’re Vulnerable or Compromised
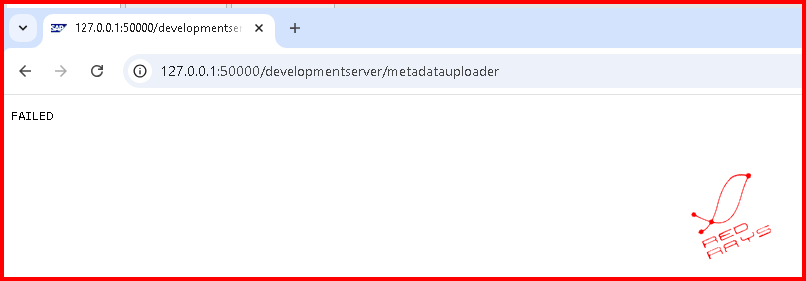
At-Risk URL Path: /developmentserver/metadatauploader
How to Determine If You’re Vulnerable
1. Check if the URL below is accessible without authentication:https://[your-sap-server]/developmentserver/metadatauploader
2. If the page opens without requiring credentials, your system is vulnerable.
Indicators of Exploitation in Logs
- Look for unauthorized access attempts to the path:
https://[your-sap-server]/developmentserver/metadatauploader - Check for unexpected file uploads in web server logs
- Search for unusual execution patterns or suspicious processes on your SAP server
- Monitor for unauthorized outbound connections from your SAP systems
If you identify any of these signs, treat your system as potentially compromised and begin your incident response procedures without delay.
Summary
SAP has recently issued a critical security patch for a severe vulnerability in the SAP NetWeaver Visual Composer, which has been actively exploited. The vulnerability, identified as CVE-2025-31324, was patched just hours ago with the release of SAP Security Note 3594142.
This high-severity flaw has been assigned a CVSS score of 10.0 (Critical), reflecting the highest possible risk. The vulnerability enables unauthenticated remote attackers to upload malicious files to vulnerable systems, potentially allowing them to execute arbitrary code and achieve full system compromise.
More: Critical SAP Zero-Day (CVE-2024-41730) Exploited by Initial Access Brokers
Vulnerability Overview
The vulnerability is located in the Metadata Uploader component of SAP NetWeaver Visual Composer. As stated in SAP’s security advisory:
| Attribute | Details |
|---|---|
| Vulnerability Type | Missing Authorization Check (CWE-434 – Unrestricted Upload of File with Dangerous Type) |
| Affected Component | EP-VC-INF (Enterprise Portal > Visual Composer > Visual Composer Infrastructure), Version 17 |
| CVSS Score | 10.0 (Critical) |
| Attack Vector | Network |
| Attack Complexity | Low |
| Privileges Required | None |
| User Interaction | None |
| Impact | High impact on confidentiality, integrity, and availability |
The root cause of this issue is the lack of proper authorization checks in the Metadata Uploader component, enabling unauthenticated attackers to upload potentially harmful executable files to vulnerable systems. If exploited, this vulnerability could result in a complete system compromise, jeopardizing the confidentiality, integrity, and availability of essential business data and applications.
In-Depth Technical Analysis
1. No Authentication Needed: Attackers can exploit this vulnerability without the need for valid credentials.
2. Low Attack Complexity: The attack is relatively simple to carry out.
3. No User Interaction Required: The exploitation does not require any action from users or administrators.
4. High Impact: Successful exploitation could grant attackers complete control over the affected system.
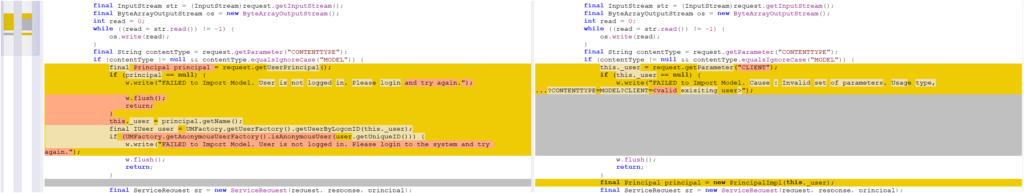
The flaw lies in the authorization mechanism of the Metadata Uploader, which fails to properly verify whether users have the necessary permissions before allowing file uploads. This weakness enables attackers to bypass security measures and upload malicious binaries, which can then be executed on the server.
Practical Implications
Organizations running vulnerable versions of SAP NetWeaver Visual Composer face significant risks. Exploiting this vulnerability could allow attackers to:
- Access sensitive business data without authorization
- Alter critical business processes
- Disrupt the availability of essential SAP services
- Maintain persistence within the network
- Move laterally to other systems within the infrastructure
Industries that rely heavily on SAP solutions, such as manufacturing, healthcare, financial services, and critical infrastructure, are especially vulnerable to this threat.
Recommended Mitigation Measures
SAP has released a security patch via Security Note 3594142. Organizations are strongly encouraged to take the following actions immediately:”
- Install the Latest Patch: Apply SAP Security Note 3594142 without delay.
- Limit Access: Restrict access to the Metadata Uploader component until patches are applied.
- Review External Exposure: Ensure that only authenticated users can upload files to SAP components.
- Implement Workaround: For organizations unable to apply the patch immediately, SAP has provided a temporary workaround based on the guidance in KBA 3593336.
Patch Information
| Support Package | Patch Version |
|---|---|
| SP033 | 000000 |
| SP028 | 000001 |
| SP029 | 000001 |
| SP030 | 000001 |
| SP031 | 000001 |
| SP027 | 000002 |
| SP032 | 000000 |
The security note includes several patches for Visual Composer Framework 7.50 in the following Support Packages.
CONCLUSION
The recently discovered CVE-2025-31324 vulnerability in SAP NetWeaver Visual Composer posed a significant threat, actively being exploited in the wild. Fortunately, SAP has quickly patched the issue with the release of SAP Security Note 3594142. Organizations using vulnerable SAP applications must update their systems immediately to prevent potential exploitation and protect critical business processes.
By verifying the exposure of vulnerable components, monitoring logs for signs of exploitation, and implementing recommended mitigation measures, organizations can secure their SAP systems and avoid the severe risks posed by this vulnerability.

